A sample application is demonstrated to explain the concept of how IDOR vulnerability works and the mitigation measures which needs to be taken by the developer.
For the sample application to work, your system should have docker and docker-compose installed. The guide to install the same can be found on Docker Installation .
Run the projectasuras/idor application using docker (the application runs on port 5000):
docker run --rm -p5000:5000 --name vuln_app projectasuras/idorNote: Docker image version shown in the guide is v1.0.0.
Now navigate to http://127.0.0.1:5000 to access the application’s web portal.
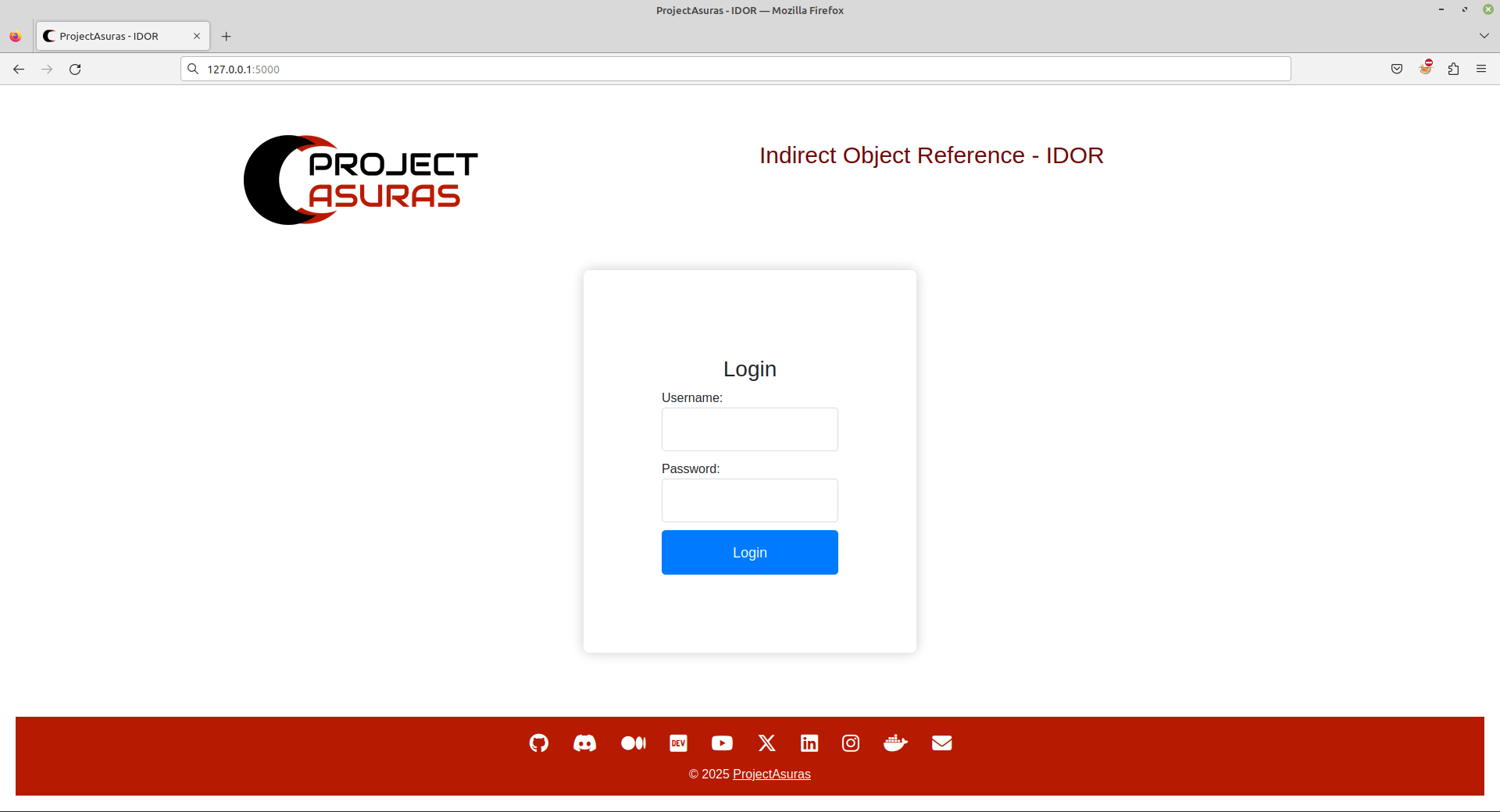
The default credentials for the application are projectasuras:projectasuras. Once, the login is successful, you will be able to view profile page of projectasuras containing critical information such as Token to make banking transactions.
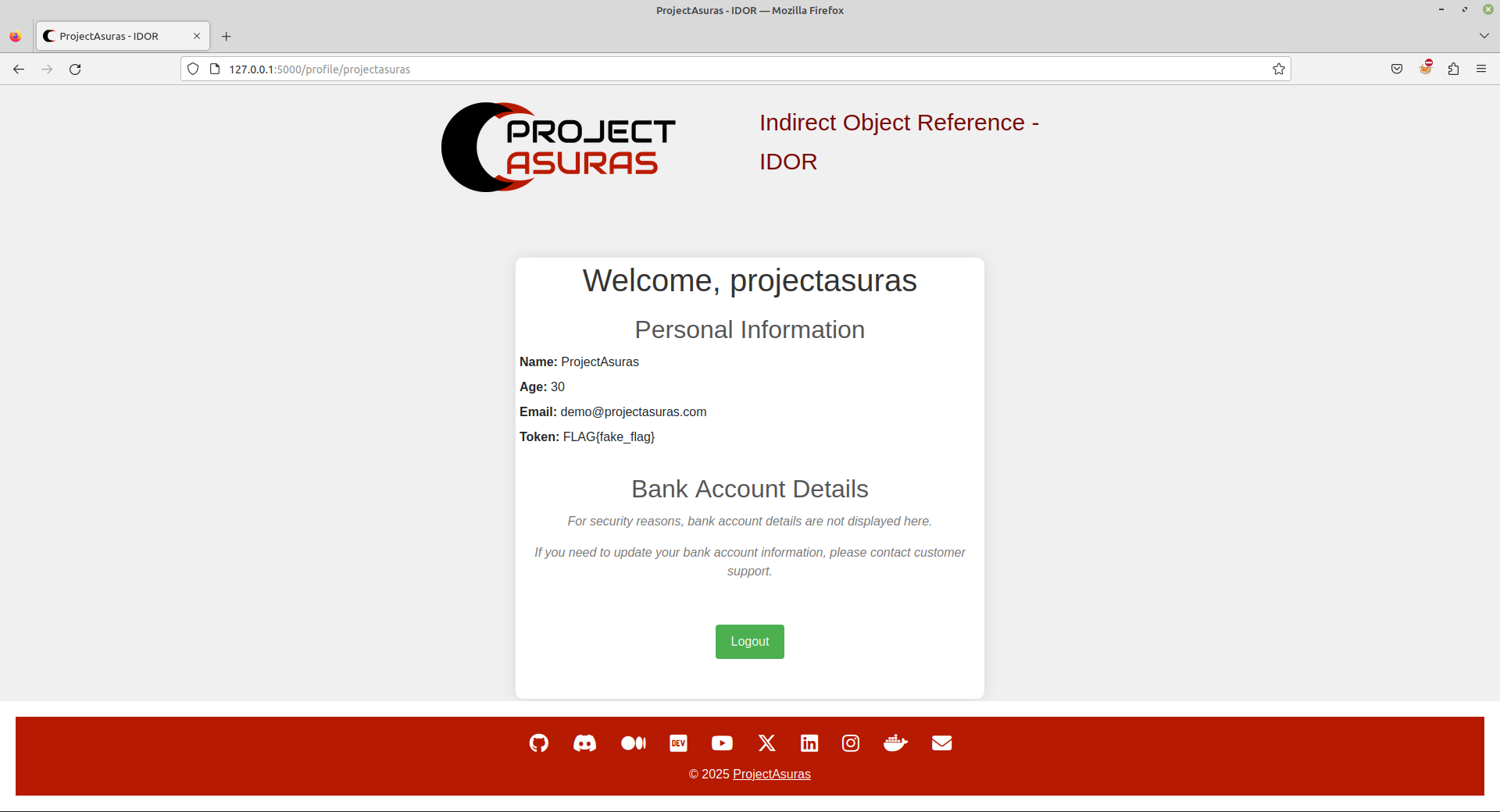
Question
Can you identify something in the URL?
The user used by us to login into the application is projectasuras and the http://127.0.0.1:5000/profile/projectasuras endpoint also contains projectasuras. It makes us wonder, can we change this parameter to view profile of other users. Let’s try to change the user to root.
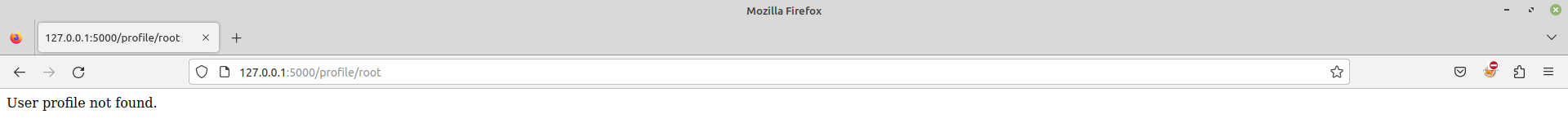
Hard luck! root user does not exist.
Note
As an attacker, we will to enumerate various combinations of username which can be present in this web application.
Let’s try another user named alice.
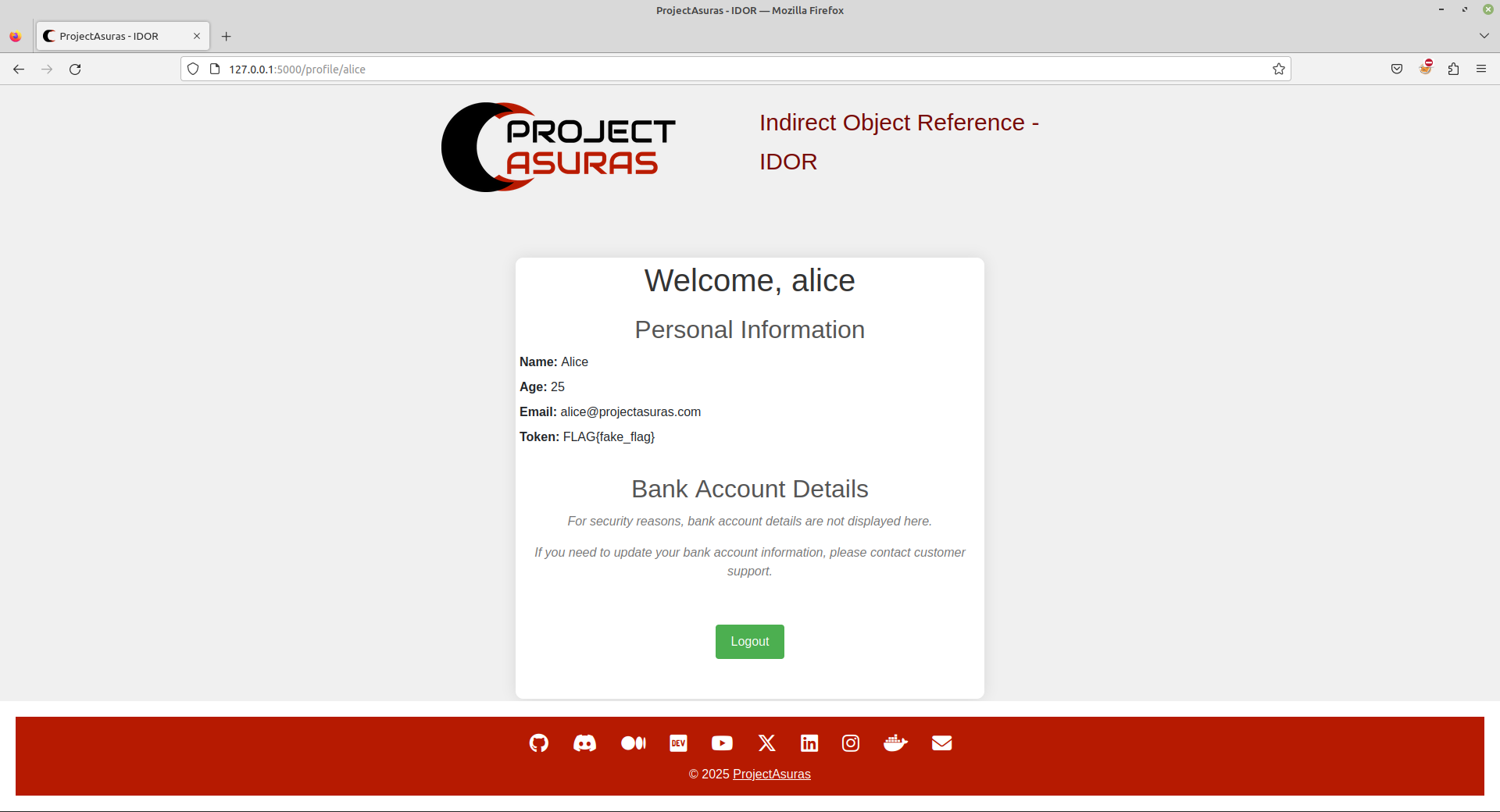
Success! We are able to access details of alice user.
Todo
Can you find any other user, and find that user’s secret TOKEN.
Question
Can you think, what mistake the developer must have made which allows anyone to access anyone’s profile?
We will answer to that question in the next part of this series.
