Server-Side Request Forgery (SSRF) is a type of security vulnerability where an attacker can manipulate a server to make requests (on attacker’s behalf) to internal or external resources. This can lead to various attacks, such as unauthorized access to internal systems, information disclosure, and more.
The steps for performing a simple SSRF attack is illustrated in the diagram below:
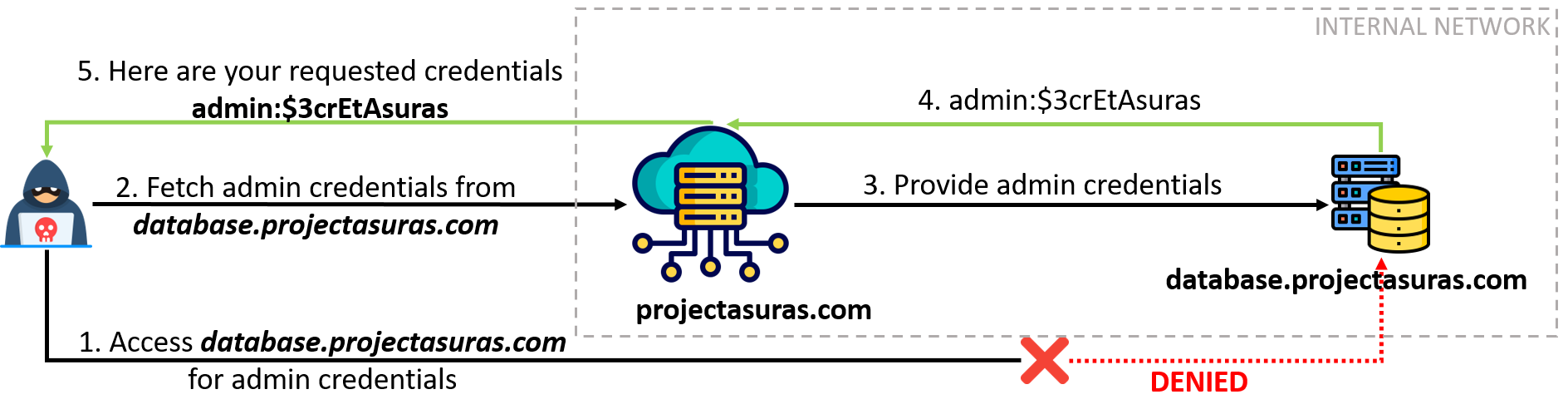
In the above diagram there are a series of steps which the attacker has performed to fetch the admin credentials from database.projectasuras.com.
- The attacker initially made an HTTP request for directly accessing the admin credentials from
database.projectasuras.com, but due to unauthorised access, the request was Denied with status code401 Unauthorized. - The attacker being a loyal reader of
projectasuras.comhave a user-level privileged account on the main website. Due to authorised user ofprojectasuras.comthe attacker tries to accessdatabase.projectasuras.comthroughprojectasuras.comas a Proxy. projectasuras.comweb server thinks this as a valid HTTP request, sends the request todatabase.projectasuras.cominternally for resolution.- Upon resolution of the request, the admin credentials of database server is returned back to
projectasuras.com - The admin credentials are then returned from
projectasuras.comback to the attacker, resulting in Information Disclosure.
In the above example, the HTTP request is forged such that the Server (projectasuras.com) internally requests an internal service (database.projectasuras.com) on-behalf of the attacker and returns back the database admin credentials. This whole attack vector is known as Server-Side Request Forgery (SSRF) attack, where a server is treated as a proxy to make vulnerable requests to other internal or external services to fetch critical information on-behalf of attacker.
In the next part of the series, we will look at an live sample application vulnerable to SSRF attack.
